Microsoft Intune facilitates Win32 app management, empowering organizations to seamlessly install, configure, secure, and monitor Windows applications across devices. Win32 apps are managed through the Microsoft Intune management extension (IME), which auto-installs when a PowerShell script or Win32 app is assigned via Intune.
Key features of Win32 app management in Intune include:
- Management of Traditional Desktop Apps: Enables management of large, traditional desktop applications.
- Support for Various App Types: Facilitates management of diverse application types.
- Control Over Complex Installations: Provides controls for managing complex app installations.
- Detection Rules, Dependencies, and Requirements: Supports defining detection rules, dependencies, and prerequisites for apps.
- Compatibility with 32-bit and 64-bit Windows: Supports both 32-bit and 64-bit Windows operating system architectures.
- Support for Windows S Mode Devices: Ensures compatibility with devices running Windows S mode.
Use the Win32 app content
Microsoft Win32 Content Prep Tool to preprocess Windows classic (Win32) apps. The tool converts application installation files into the .intunewin format. The tool also detects some of the attributes that Intune requires to determine the application installation state. After you use this tool on the app installer folder, you’ll be able to create a Win32 app in the Microsoft Intune admin center.
Process flow to create a .intunewin file
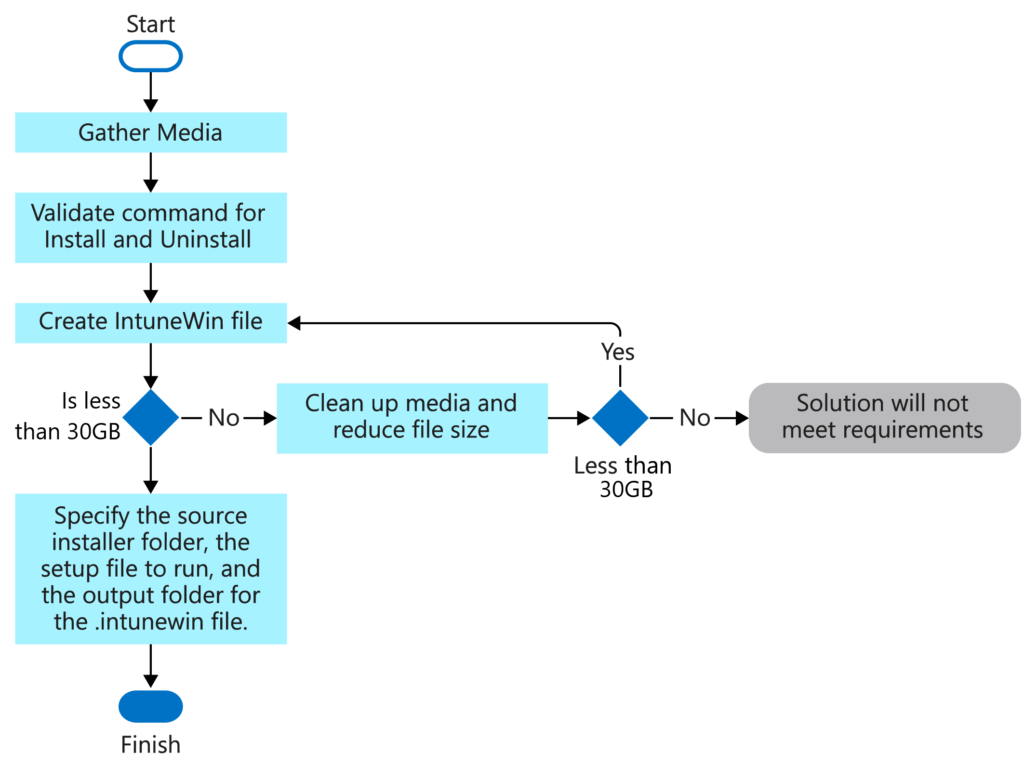
The flow behind delivery of a Win32 app to client

- If you want to see the contents of the
.intunewinfile after the file is created, rename its extension to.zip. - The
.intunewinfile contains two folders: Contents and Metadata. Contents folders contain the application package (the installer .intunewin), and theDetection.xmlfile (containing the file encryption information).
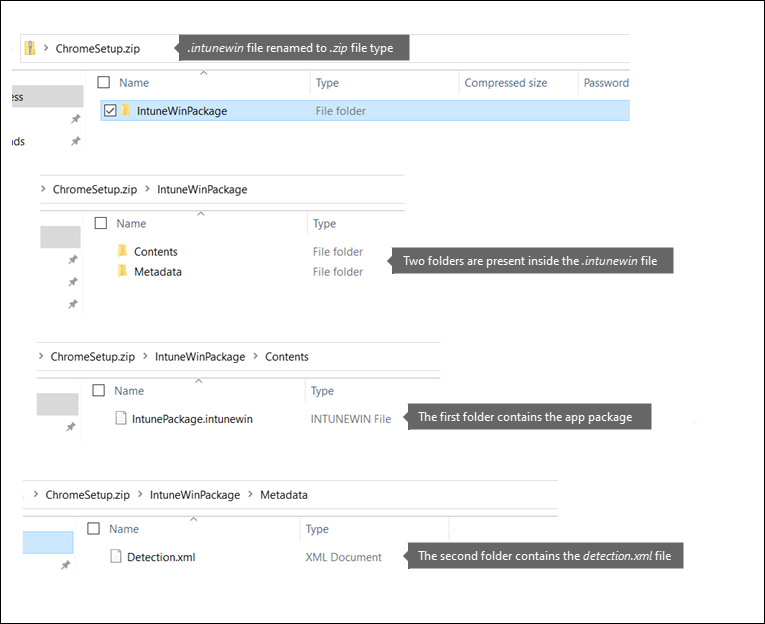
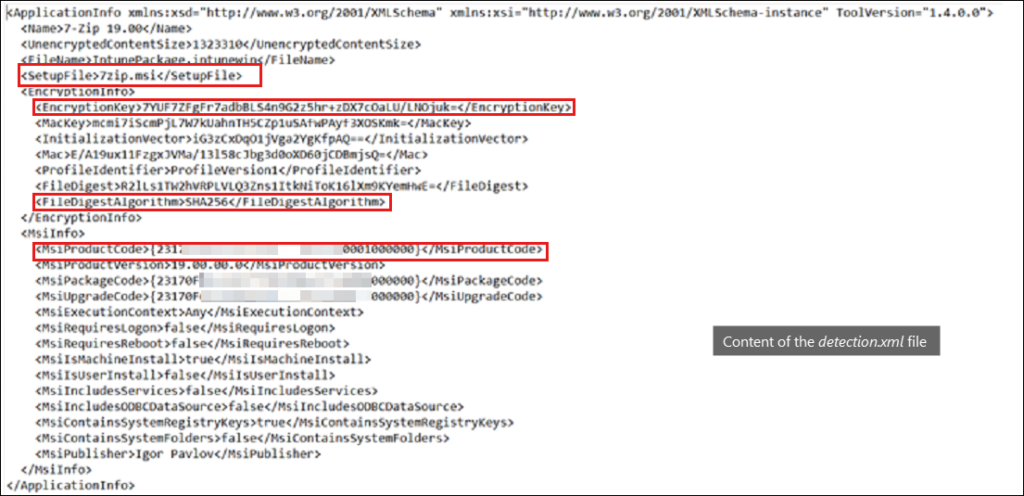
Win32 application processing at the device end
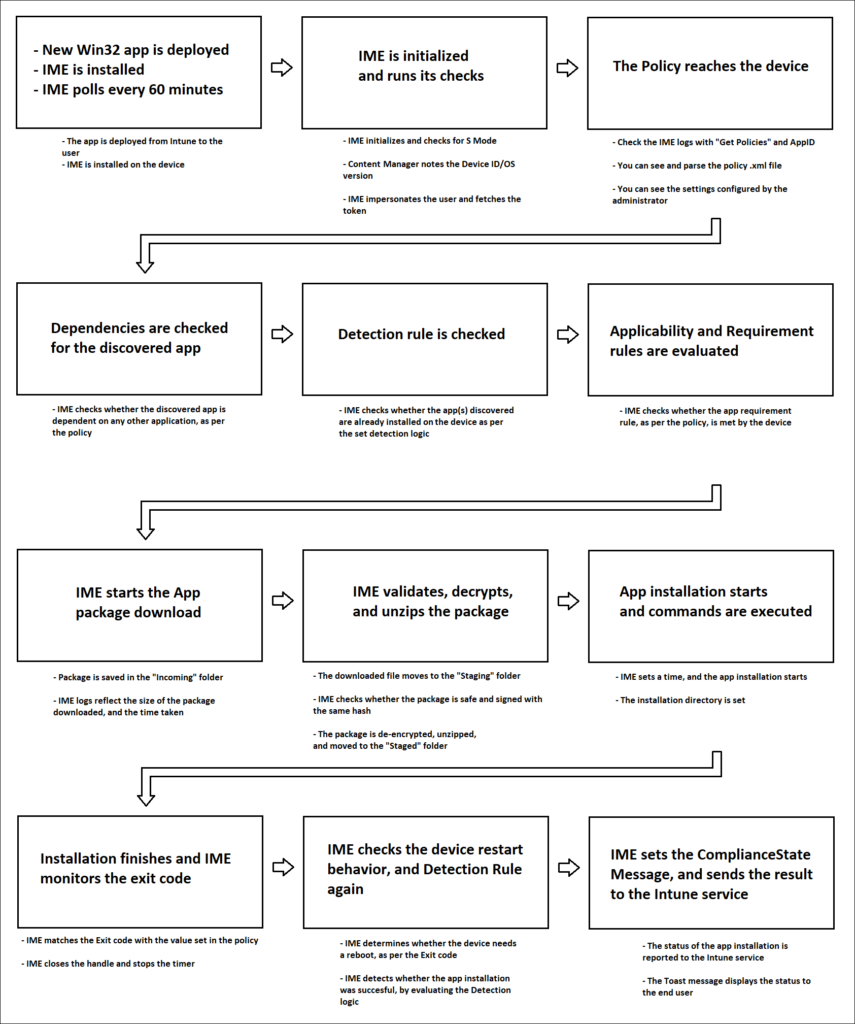
Logs
Here is the location of the log file of Intune Management Extension:
This location mainly contains the following log files that track the described information:
- AgentExecutor.log: This logfile tracks PowerShell script executions (deployed by Intune).
- ClientHealth.log: This logfile tracks the sidecar agent-client health activities.
- IntuneManagementExtension.log: The IME log that tracks all the flow that is illustrated in the following steps.
- AppWorkload.log: is a new log file introduced in Intune service release 2408. It helps troubleshoot and analyze Win32 app management events on the client. This log file contains all the logging data related to Win32 app deployment activities carried out by the Intune Management Extension (IME)
Detailed flow in IME Logs
Here is the detailed flow behind the processing of a Win32 app at the device end, as viewed in the IME logs. The steps are listed in the sequence of occurrence.Expand table
| Step | Message in the log | Explanation |
|---|---|---|
| 1 | Intune Management Extension gets initialized. | EMS Agent is started. |
| 2 | S Mode is checked. | |
| 3 | Content manager starts. | |
| 4 | Deviceid and OS version is noted. | |
| 5 | IME discovers the endpoint of Intune (CDNs) | Approve these items in the firewall (if blocked) as stated in the network pre-requisites listed earlier. |
| 6 | Impersonation for the user occurs, and token is requested or granted. | |
| 7 | PUT request is sent. | |
| 8 | You see a Get Policies response that contains the entire policy body (as configured by the admin in the portal). | You can check to make sure that the policy that is received by IME is in accordance with the configured policy. |
| 9 | ExecManager identifies the app name/appid/app installation intent. | |
| 10 | Dependency is checked for the apps that were discovered. | If dependencies are discovered, the dependent app is downloaded and installed first. |
| 11 | Detection rules are checked for the apps. | Detection rule as set in the policy is evaluated. If the app is detected in the device at this stage, the download and installation attempt of the app (in the following step) is skipped. |
| 12 | Applicability is checked for the app (requirement and extended requirement). | You can use a Powershell script as well (needs to be uploaded to the Intune portal) to run this requirement check. |
| 13 | Download starts by sending a toast notification. | User can see an intuitive notice in the device that indicates that the app is downloading and installing. |
| 14 | Download job is created and timer is set. | |
| 15 | Content is downloaded to C:\Program Files (x86)\Microsoft Intune Management Extension\Content\Incoming\59f9a567-b92d-4dc2-9c7a-fdb94e29275c_1.bin. | |
| 16 | Download job finishes, time taken is noted, bytes download is noted, job is closed. | |
| 17 | Verification of encrypted hash, decryption starts. | |
| 18 | Unzipping starts from Content\Staging to C:\Windows\IMECache\59f9a567-b92d-4dc2-9c7a-fdb94e29275c_1. | |
| 19 | Organize staging content. | |
| 20 | Installer execution starts. | |
| 21 | Prepare .msi cmdline for system context. | |
| 22 | msiexec /i "7zip.msi" /q /qn ALLUSERS=1 REBOOT=ReallySuppress /norestart | Command is specified by the admin for the app in the portal. |
| 23 | Installation finishes, results collected. | |
| 24 | lpExitCode 0, determines whether it’s a success. | |
| 25 | DeviceRestartBehavior: 2 (checks , device restart behavior) handle is closed. | Device restart action as stated in the policy that is defined by the admin in the portal. |
| 26 | The detection rule starts by SideCarFileDetectionManager | The detection rule evaluated in Step 11 is evaluated again after the app installation. |
| 27 | Checked under path: C:\Temp, file Path: C:\Temp\7zip, agent was checking under expanded: C:\Temp\7zip, applicationDetected: True. | |
| 28 | Set ComplianceStateMessage and application detected after execution. | |
| 29 | EnforcementStateMessage: determines the output after the detection process, toast message of the installation status is sent again. | User can see an intuitive notice in the device that indicates that the app installed successfully or failed (as applicable). |
| 30 | Organize staged content.C:\Windows\IMECache\59f9a567-b92d-4dc2-9c7a-fdb94e29275c_1. | |
| 31 | Start reporting app results. | |
| 32 | Send results to service. | The Intune admin can view the status of App deployment for the device in the Intune portal. |